Cybersecurity Strategy Management Framework
This article is part of the Cybersecurity Strategy Management Framework. The work on it is currently in progress. You can read more about the framework in this article.
Objectives
Activities

Identify stakeholders
Cybersecurity strategy stakeholders are people or groups engaged in its development, interested in it, who can influence its shape, or will be impacted by it. Some project managers also add to this group people who are not directly affected by the initiative but perceive themselves as being impacted.
In smaller organizations, you can identify them by conducting simple desk-based research. In bigger companies, it will be more beneficial to engage your strategy development team and identify relevant stakeholders during a dedicated workshop.
No matter what your approach will be, you can start by asking yourself or the whole team the following questions.
Questions to identify cybersecurity stakeholders
- Who is and who should be in the strategy development team?
- Who will provide the budget and other resources for strategy execution?
- Whose cooperation will you need to drive its implementation?
- Who will receive and approve the strategy?
- Who will be its ultimate owner?
- Who will be interested in the strategy?
- Who will be affected by it?
- Who can influence it?
- Whose opposition may hinder your progress?
- Who is the source of requirements for cybersecurity?
- Who are the subject matter experts that will participate?
Think about internal as well as external stakeholders. To identify internal stakeholders, start with your organizational chart. To determine external ones, look at various relations that your company has.
You can use the following list as your starting point. Please note that it is not exhaustive and that its items are displayed in alphabetical order.
Internal stakeholders
External stakeholders
These are essential stakeholders you should recognize when preparing for the development of a cybersecurity strategy. The number and nature of stakeholders relevant to your situation will depend on your industry, the size of your organization, and its cybersecurity maturity.
Here are a couple of tips for identifying strategy stakeholders:
Focus on discovery. Your main objective at this stage is to scan your strategic environment and identify all stakeholders. Refrain from discussions about stakeholder characteristics and justification for their selection. If you keep the discovery perspective and continue listing stakeholders, you will get more complete results. You can refine your list later.
Do not overlook important stakeholders. Ensure that you have the most critical stakeholders. If you miss major stakeholders, you may need to revise your strategic assumptions later, delaying the strategy development process.
Use agile approach. Your initial list may expand. You may uncover further stakeholders during interviews with those already identified. You may also need to update your stakeholder list and analysis during other stages of strategy management.
Identify representatives. When you identify a group of stakeholders, consider also determining its representative. It will help you keep a manageable list of attendees when scheduling interviews, meetings, or workshops.
| Stakeholder | Representative | Tier |
|---|---|---|
| CEO | - | Internal |
| CFO | - | Internal |
| CTO | - | Internal |
| Data Protection Agency | Andy Smith | External |
| Employees | Casey Jones | Internal |
| Information Owners | Jassie Miller | Internal |

Refine stakeholder list
Review your initial list and verify if it is granular enough. Avoid leaving big aggregates of stakeholders that have different characteristics in terms of power or interest. For example, you may have different tiers of suppliers, and the strategy impact on them will be different.
In this scenario, it may be beneficial to divide “all suppliers” into separate groups for relevant third-party tiers. In some instances, you may also have individuals who will be managed more effectively as separate stakeholders instead of part of a wider group.

Create a stakeholder matrix
There are different tools to visualize stakeholder characteristics. They include Stakeholder Sector Analysis, Salience Model, Influence-Involvement Grid, Power-Influence Grid, Stakeholders Map, and many more. You can read about them in the books listed in the Reference section of this article if you would like to deepen your knowledge about stakeholder management.
However, the most simple and usable at this stage is Power-Interest Grid. It helps to visualize stakeholder power and interest, identify key stakeholders and make decisions about required stakeholder management activities.
To develop a stakeholder matrix, draw a chart with the Power and Interest axes as illustrated in the following picture. Use a scale of 1 to 10 on each axis or any other scale that will fit your needs in terms of granularity you would like to achieve.

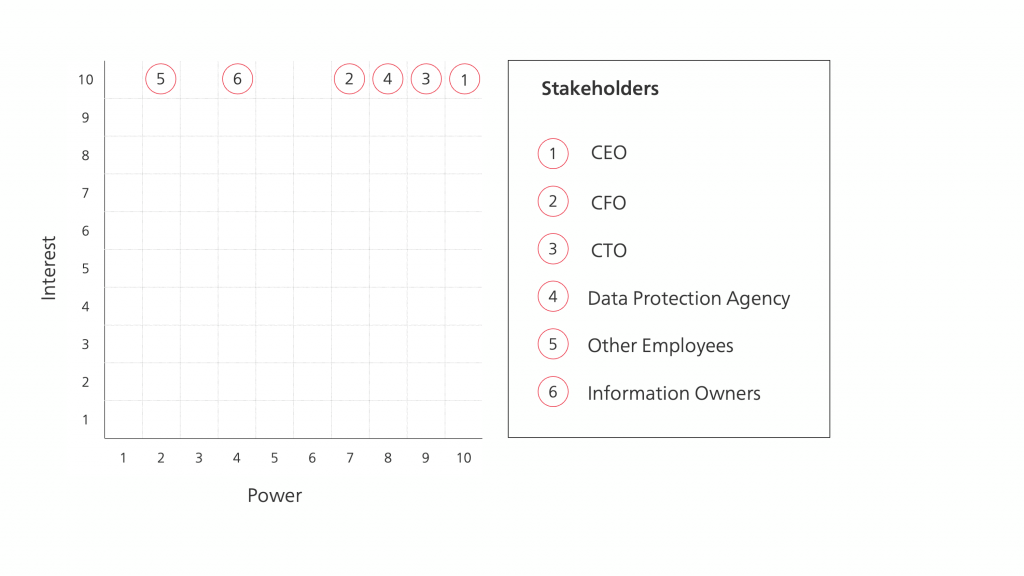
Determine stakeholder power
Understanding your stakeholders’ influence means understanding their power over your cybersecurity strategy. This Stakeholder power is the ability to influence people’s behaviors and get things done. Stakeholders with a high level of power can influence critical decisions during cybersecurity strategy definition, provide resources for its implementation and motivate people to take necessary actions.
To understand the level of stakeholder influence, consider their formal and informal power. The formal power will typically be bound to stakeholder position within the organizational structure and their authority regarding cybersecurity. The informal power will often be exercised by networks your stakeholders have built with the rest of the organization and their observed reputation.
You can assess the level of influence by asking the following questions.
Questions to assess stakeholder power
- How high is the stakeholder in organizational structure?
- What is the perceived importance of their department?
- What is his or her formal authority over cybersecurity?
- What is their influence on cybersecurity resources?
- What informal power do they have through their networks?
- What are their leadership skills?
Next, position each of the analyzed stakeholders on the power axis of your stakeholder matrix. The easiest way of doing it is to place the most powerful person on the right side of the grid, the least powerful person on the left side, and use their positions as anchor points for putting remaining stakeholders. You can also create low, medium, and high power ranges and place stakeholders inside them. These positions do not have to be precise. The purpose is to classify stakeholders according to their power quickly and efficiently.

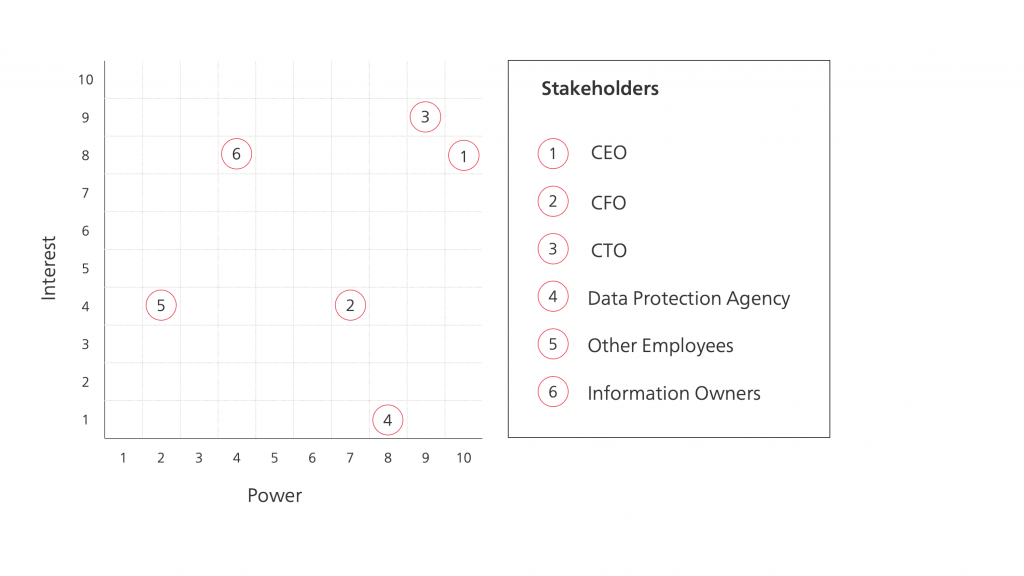
Determine stakeholder interest
To have a better picture of your stakeholders, you also need to assess their interest in the strategy. You can measure it by determining how the cybersecurity strategy will impact them. You can also estimate it by evaluating the extent to which the strategy must address their needs to become successfully executed.
You may not have enough information to make a final decision at this stage, so make your best call using professional judgment. Make initial assumptions about what may follow after strategy implementation.
Consider the following questions.
Questions to assess stakeholder interest
- How important are their needs and expectations for strategy success?
- What is the level of common interests between them and strategy?
- To which point can the strategy impact their roles?
- To which degree could they benefit or lose because of the strategy?
- How could their duties change?
- How could their expected behaviors change?
After considering these questions, you should move your stakeholders on the stakeholder matrix along the interest axis. Similarly, as before, you can identify most and least interested, put them in relevant positions and use them as anchor points for positioning remaining stakeholders.
You will have to update this assessment after the “2d. Define target state model” activity because then you will have a better sense of proposed changes and their impact on specific stakeholders.

Determine stakeholder tiers
Using the stakeholder matrix presented in “Managing Strategy: Mapping Out Strategic Success,” you can distinguish four stakeholder groups.
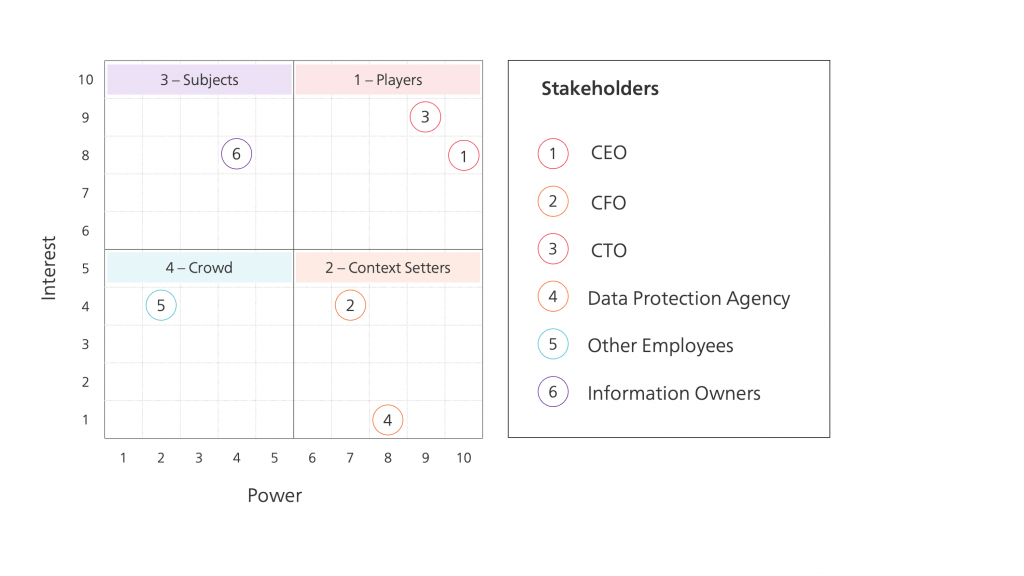
Stakeholder tiers
Grouping your stakeholders into tiers presented above will help define collaboration plans described in “1d. Define collaboration plan” activity.

Update stakeholder inventory
At the end of this activity, you can update your stakeholder register with details that you collected, including stakeholder power and interest levels as well as their tiering.
| Stakeholder | Power | Interest | Tier |
|---|---|---|---|
| CEO | 10 | 7 | Players |
| CFO | 8 | 4 | Context Setters |
| CTO | 9 | 10 | Players |
| Data Protection Agency | 8 | 1 | Context Setters |
| Employees | 2 | 4 | Subjects |
| Information Owners | 4 | 8 | Crowd |
Outputs
References
Use the following links to deepen your knowledge about this topic.
Cybersecurity Strategy Management Framework
This article is part of the Cybersecurity Strategy Management Framework. The work on it is currently in progress. You can read more about the framework in this article.
